分类:运维技术日期:2021-04-16 - 14:15:38评论:1条作者:老谢
原理是利用oxidized的hooks功能调用zabbix_sender推送数据给zabbix_server。
oxidized的config部分
hooks:
node_success:
type: exec
events: [node_success]
cmd: '
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k oxidized.datetime -o `date +%s`;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k oxidized.status -o 0;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_EVENT -o $OX_EVENT;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_JOB_STATUS -o $OX_JOB_STATUS;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_JOB_TIME -o $OX_JOB_TIME;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_IP -o $OX_NODE_IP;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_MODEL -o $OX_NODE_MODEL;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_NAME -o $OX_NODE_NAME'
async: false
timeout: 120
node_fail:
type: exec
events: [node_fail]
cmd: '
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k oxidized.datetime -o `date +%s`;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_EVENT -o $OX_EVENT;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_JOB_STATUS -o $OX_JOB_STATUS;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_JOB_TIME -o $OX_JOB_TIME;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_IP -o $OX_NODE_IP;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_MODEL -o $OX_NODE_MODEL;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_NAME -o $OX_NODE_NAME;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k oxidized.status -o 1'
async: false
timeout: 120
post_store:
type: exec
events: [post_store]
cmd: '
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k oxidized.datetime -o `date +%s`;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_EVENT -o $OX_EVENT;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_JOB_STATUS -o $OX_JOB_STATUS;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_JOB_TIME -o $OX_JOB_TIME;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_IP -o $OX_NODE_IP;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_MODEL -o $OX_NODE_MODEL;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_NAME -o ${OX_NODE_NAME};
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k oxidized.status -o 2'
async: false
timeout: 120 |
hooks:
node_success:
type: exec
events: [node_success]
cmd: '
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k oxidized.datetime -o `date +%s`;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k oxidized.status -o 0;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_EVENT -o $OX_EVENT;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_JOB_STATUS -o $OX_JOB_STATUS;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_JOB_TIME -o $OX_JOB_TIME;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_IP -o $OX_NODE_IP;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_MODEL -o $OX_NODE_MODEL;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_NAME -o $OX_NODE_NAME'
async: false
timeout: 120
node_fail:
type: exec
events: [node_fail]
cmd: '
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k oxidized.datetime -o `date +%s`;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_EVENT -o $OX_EVENT;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_JOB_STATUS -o $OX_JOB_STATUS;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_JOB_TIME -o $OX_JOB_TIME;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_IP -o $OX_NODE_IP;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_MODEL -o $OX_NODE_MODEL;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_NAME -o $OX_NODE_NAME;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k oxidized.status -o 1'
async: false
timeout: 120
post_store:
type: exec
events: [post_store]
cmd: '
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k oxidized.datetime -o `date +%s`;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_EVENT -o $OX_EVENT;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_JOB_STATUS -o $OX_JOB_STATUS;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_JOB_TIME -o $OX_JOB_TIME;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_IP -o $OX_NODE_IP;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_MODEL -o $OX_NODE_MODEL;
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k OX_NODE_NAME -o ${OX_NODE_NAME};
/usr/local/zabbix/bin/zabbix_sender -z zabbix_server_ip -s zabbix_agentd(server_name) -k oxidized.status -o 2'
async: false
timeout: 120
继续阅读…
分类:运维技术日期:2021-04-10 - 18:35:51评论:0条作者:老谢
Zabbix MySQL Database Partitioning 表分区优化禁用 housekeeping 提升历史数据清理性能
Zabbix 默认会启用 housekeeping 功能用于清理 history/trend 等历史数据,当监控服务器数量增加,保留时间有要求的情况下,housekeeping 的清理策略就会造成 Zabbix Server 性能下降,比如查询历史监控数据等。Zabbix 官方的建议是直接在数据库按照时间唯独创建分区表并定时清理,好处自然就是减少 Zabbix Server 的负担提升 Zabbix 应用对于数据库读写性能。Zabbix 3.4 之后的版本增加了对 Elasticsearch 的支持。
数据库的优化有横向和纵向扩展,这里使用数据的分布式,而分表可以看做是分布式的一种。。
在zabbix_server.conf文件中,找到如下两个参数:
(1)HousekeepingFrequency=1 解释:多久删除一次数据库里面的过期数据(间隔时间),默认一小时
(2)MaxHousekeeperDelete=5000 解释:每次删除数据量的上线(最大删除量),默认5000
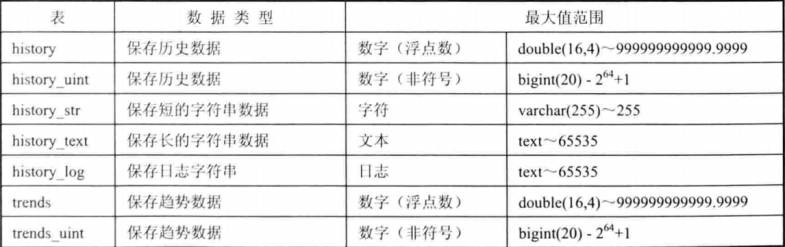
SELECT table_name AS "Tables",
round(((data_length + index_length) / 1024 / 1024), 2) "Size in MB"
FROM information_schema.TABLES
WHERE table_schema = 'zabbix'
ORDER BY (data_length + index_length) DESC;
+----------------------------+------------+
| Tables | Size in MB |
+----------------------------+------------+
| history_uint | 16452.17 |
| history | 3606.36 |
| history_str | 2435.03 |
| trends_uint | 722.48 |
| trends | 176.28 |
| history_text | 10.03 |
| alerts | 7.47 |
| items | 5.78 |
| triggers | 3.72 |
| events | 2.64 |
| images | 1.53 |
| items_applications | 0.70 |
| item_discovery | 0.58 |
| functions | 0.53 |
| event_recovery | 0.38 |
| item_preproc | 0.38 |
……………… |
SELECT table_name AS "Tables",
round(((data_length + index_length) / 1024 / 1024), 2) "Size in MB"
FROM information_schema.TABLES
WHERE table_schema = 'zabbix'
ORDER BY (data_length + index_length) DESC;
+----------------------------+------------+
| Tables | Size in MB |
+----------------------------+------------+
| history_uint | 16452.17 |
| history | 3606.36 |
| history_str | 2435.03 |
| trends_uint | 722.48 |
| trends | 176.28 |
| history_text | 10.03 |
| alerts | 7.47 |
| items | 5.78 |
| triggers | 3.72 |
| events | 2.64 |
| images | 1.53 |
| items_applications | 0.70 |
| item_discovery | 0.58 |
| functions | 0.53 |
| event_recovery | 0.38 |
| item_preproc | 0.38 |
………………
继续阅读…
分类:运维技术日期:2021-03-17 - 22:13:47评论:1条作者:老谢
安装部署
实实在在不想用ubuntu server,为了后面配合zabbix做配置变更的告警出发,docker后期的配置zabbix会更麻烦,所以经过一天的折腾,oxidized成功部署在了centos7.9上,docker的部署方式在本文后半段,需要的话请往后面翻。
系统版本号:CentOS Linux release 7.9.2009 (Core)
部署步骤
yum update
#更新前,建议更换国内yum源,开局可以直接更新,正式放到生产后不建议使用update更新所有rpm包
#记得关闭selinux
yum install centos-release-scl
#安装centos-release-scl软件源
yum install rh-ruby23 rh-ruby23-ruby-devel
#安装ruby2.3版本,系统自带为2.0的ruby
scl enable rh-ruby23 bash
#这一步非常重要,开启ruby的环境变量,否则oxidized无法启动
yum install make cmake which sqlite-devel openssl-devel libssh2-devel ruby gcc ruby-devel libicu-devel gcc-c++
#安装相关的依赖
gem install oxidized
#安装主角
gem install oxidized-script oxidized-web
#安装web界面
ruby -v
[root@localhost ~]# ruby -v
ruby 2.3.8p459 (2018-10-18 revision 65136) [x86_64-linux]
#检查ruby版本是否正确,应大于2.3
which ruby
[root@localhost ~]# which ruby
/opt/rh/rh-ruby23/root/usr/bin/ruby
#检查ruby路径
vim /etc/profile.d/rh-ruby22.sh
#!/bin/bash
source /opt/rh/rh-ruby23/enable
export X_SCLS="`scl enable rh-ruby23 'echo $X_SCLS'`"
export PATH=$PATH:/opt/rh/rh-ruby23/root/usr/bin/ruby
#配置环境变量的自启动
ln -s /opt/rh/rh-ruby23/root/usr/local/bin/oxidized /usr/local/bin/oxidized
vim /lib/systemd/system/oxidized.service
# /lib/systemd/system/oxidized.service
[Unit]
Description=Oxidized - Network Device Configuration Backup Tool
After=network-online.target multi-user.target
Wants=network-online.target
[Service]
ExecStart=/usr/local/bin/oxidized
KillSignal=SIGKILL
User=root
[Install]
WantedBy=multi-user.target
#以上使用root用户运行oxidized,一定要确保已经做了/usr/local/bin/oxidized的ls链接
chmod +x /lib/systemd/system/oxidized.service
vi /etc/ld.so.conf
#增加 /opt/rh/rh-ruby23/root/usr/lib64
ldconfig
ldconfig -v
#检查有没有ruby的so库
chmod +x /lib/systemd/system/oxidized.service
#接着需要创建router.db和config配置文件,这些请参考以下docker的配置流程,完全一致
[root@localhost ~]# systemctl enable oxidized.service
Created symlink from /etc/systemd/system/multi-user.target.wants/oxidized.service to /usr/lib/systemd/system/oxidized.service.
[root@localhost ~]# systemctl start oxidized.service
[root@localhost ~]# systemctl status oxidized.service
● oxidized.service - Oxidized - Network Device Configuration Backup Tool
Loaded: loaded (/usr/lib/systemd/system/oxidized.service; disabled; vendor preset: disabled)
Active: active (running) since Wed 2021-03-24 18:59:37 CST; 2s ago
Main PID: 6767 (oxidized)
CGroup: /system.slice/oxidized.service
└─6767 puma 3.11.4 (tcp://0.0.0.0:8888) [/]
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: I, [2021-03-24T18:59:37.635254 #6767] INFO -- : Oxidized starting, running as pid 6767
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: I, [2021-03-24T18:59:37.635810 #6767] INFO -- : lib/oxidized/nodes.rb: Loading nodes
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: I, [2021-03-24T18:59:37.711327 #6767] INFO -- : lib/oxidized/nodes.rb: Loaded 1 nodes
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: Puma starting in single mode...
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: * Version 3.11.4 (ruby 2.3.8-p459), codename: Love Song
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: * Min threads: 0, max threads: 16
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: * Environment: development
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: * Listening on tcp://0.0.0.0:8888
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: Use Ctrl-C to stop
Mar 24 18:59:39 localhost.localdomain oxidized[6767]: W, [2021-03-24T18:59:39.990844 #6767] WARN -- : /192.168.1.1 status no_connection, retry attempt 1
[root@localhost ~]#
firewall-cmd --zone=public --add-port=8585/tcp --permanent
systemctl reload firewalld.service |
yum update
#更新前,建议更换国内yum源,开局可以直接更新,正式放到生产后不建议使用update更新所有rpm包
#记得关闭selinux
yum install centos-release-scl
#安装centos-release-scl软件源
yum install rh-ruby23 rh-ruby23-ruby-devel
#安装ruby2.3版本,系统自带为2.0的ruby
scl enable rh-ruby23 bash
#这一步非常重要,开启ruby的环境变量,否则oxidized无法启动
yum install make cmake which sqlite-devel openssl-devel libssh2-devel ruby gcc ruby-devel libicu-devel gcc-c++
#安装相关的依赖
gem install oxidized
#安装主角
gem install oxidized-script oxidized-web
#安装web界面
ruby -v
[root@localhost ~]# ruby -v
ruby 2.3.8p459 (2018-10-18 revision 65136) [x86_64-linux]
#检查ruby版本是否正确,应大于2.3
which ruby
[root@localhost ~]# which ruby
/opt/rh/rh-ruby23/root/usr/bin/ruby
#检查ruby路径
vim /etc/profile.d/rh-ruby22.sh
#!/bin/bash
source /opt/rh/rh-ruby23/enable
export X_SCLS="`scl enable rh-ruby23 'echo $X_SCLS'`"
export PATH=$PATH:/opt/rh/rh-ruby23/root/usr/bin/ruby
#配置环境变量的自启动
ln -s /opt/rh/rh-ruby23/root/usr/local/bin/oxidized /usr/local/bin/oxidized
vim /lib/systemd/system/oxidized.service
# /lib/systemd/system/oxidized.service
[Unit]
Description=Oxidized - Network Device Configuration Backup Tool
After=network-online.target multi-user.target
Wants=network-online.target
[Service]
ExecStart=/usr/local/bin/oxidized
KillSignal=SIGKILL
User=root
[Install]
WantedBy=multi-user.target
#以上使用root用户运行oxidized,一定要确保已经做了/usr/local/bin/oxidized的ls链接
chmod +x /lib/systemd/system/oxidized.service
vi /etc/ld.so.conf
#增加 /opt/rh/rh-ruby23/root/usr/lib64
ldconfig
ldconfig -v
#检查有没有ruby的so库
chmod +x /lib/systemd/system/oxidized.service
#接着需要创建router.db和config配置文件,这些请参考以下docker的配置流程,完全一致
[root@localhost ~]# systemctl enable oxidized.service
Created symlink from /etc/systemd/system/multi-user.target.wants/oxidized.service to /usr/lib/systemd/system/oxidized.service.
[root@localhost ~]# systemctl start oxidized.service
[root@localhost ~]# systemctl status oxidized.service
● oxidized.service - Oxidized - Network Device Configuration Backup Tool
Loaded: loaded (/usr/lib/systemd/system/oxidized.service; disabled; vendor preset: disabled)
Active: active (running) since Wed 2021-03-24 18:59:37 CST; 2s ago
Main PID: 6767 (oxidized)
CGroup: /system.slice/oxidized.service
└─6767 puma 3.11.4 (tcp://0.0.0.0:8888) [/]
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: I, [2021-03-24T18:59:37.635254 #6767] INFO -- : Oxidized starting, running as pid 6767
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: I, [2021-03-24T18:59:37.635810 #6767] INFO -- : lib/oxidized/nodes.rb: Loading nodes
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: I, [2021-03-24T18:59:37.711327 #6767] INFO -- : lib/oxidized/nodes.rb: Loaded 1 nodes
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: Puma starting in single mode...
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: * Version 3.11.4 (ruby 2.3.8-p459), codename: Love Song
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: * Min threads: 0, max threads: 16
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: * Environment: development
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: * Listening on tcp://0.0.0.0:8888
Mar 24 18:59:37 localhost.localdomain oxidized[6767]: Use Ctrl-C to stop
Mar 24 18:59:39 localhost.localdomain oxidized[6767]: W, [2021-03-24T18:59:39.990844 #6767] WARN -- : /192.168.1.1 status no_connection, retry attempt 1
[root@localhost ~]#
firewall-cmd --zone=public --add-port=8585/tcp --permanent
systemctl reload firewalld.service
如果不配置router.db是无法启动oxidized服务的,NGINX、时间等其他问题,也都和docker部署配置一致,请往下参考即可,最后请记得关闭防火墙或放行oxidized的web端口:)
继续阅读…
分类:虚拟化日期:2020-11-17 - 12:32:46评论:0条作者:老谢
测试期间直接删除了composer服务器,导致link clone生成的replica-xxx命令的副本母机无法删除,需要先解除保护后才能从VCSA中。
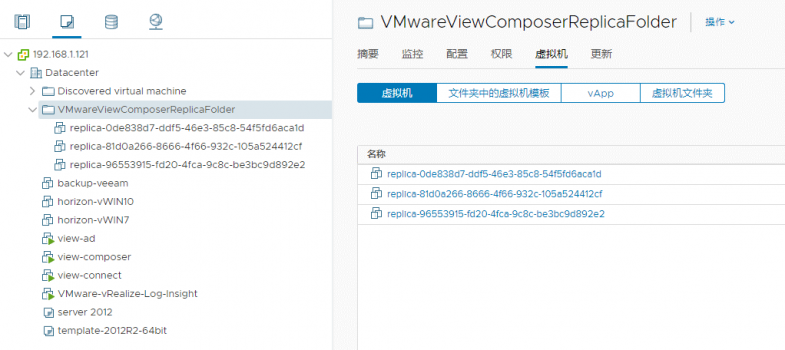
登录composer服务器,停用掉view composer服务,接着cmd先cd到C:\Program Files (x86)\VMware\VMware View Composer目录下,执行以下命令:
SviConfig -operation=UnprotectEntity -VcUrl=https://VC地址/sdk -DsnName=数据库名 -DbUsername=sa -DbPassword=SA密码 -VcUsername=Administrator@vsphere.local -VcPassword=VC密码 -InventoryPath="/Datacenter/vm/VMwareViewComposerReplicaFolder/replica-96553915-fd20-4fca-9c8c-be3bc9d892e2" -Recursive=true |
SviConfig -operation=UnprotectEntity -VcUrl=https://VC地址/sdk -DsnName=数据库名 -DbUsername=sa -DbPassword=SA密码 -VcUsername=Administrator@vsphere.local -VcPassword=VC密码 -InventoryPath="/Datacenter/vm/VMwareViewComposerReplicaFolder/replica-96553915-fd20-4fca-9c8c-be3bc9d892e2" -Recursive=true
继续阅读…
分类:运维技术日期:2020-11-13 - 13:33:23评论:1条作者:老谢
现使用的fortigate防火墙软件版本有bug导致fortiview的流量分析经常报错,但因设备托管在机房不考虑到远程升级存在风险,所以还是考虑将防火墙日志通过syslog输出给日志平台进行分析处理。
ELK简介
ELK 不是一款软件,而是 Elasticsearch、Logstash 和 Kibana 三种软件产品的首字母缩写。这三者都是开源软件,通常配合使用,而且又先后归于 Elastic.co 公司名下,所以被简称为 ELK Stack。根据 Google Trend 的信息显示,ELK Stack 已经成为目前最流行的集中式日志解决方案。
Elasticsearch:分布式搜索和分析引擎,具有高可伸缩、高可靠和易管理等特点。基于 Apache Lucene 构建,能对大容量的数据进行接近实时的存储、搜索和分析操作。通常被用作某些应用的基础搜索引擎,使其具有复杂的搜索功能;
Logstash:数据收集引擎。它支持动态的从各种数据源搜集数据,并对数据进行过滤、分析、丰富、统一格式等操作,然后存储到用户指定的位置;
Kibana:数据分析和可视化平台。通常与 Elasticsearch 配合使用,对其中数据进行搜索、分析和以统计图表的方式展示;
Filebeat:ELK 协议栈的新成员,一个轻量级开源日志文件数据搜集器,基于 Logstash-Forwarder 源代码开发,是对它的替代。在需要采集日志数据的 server 上安装 Filebeat,并指定日志目录或日志文件后,Filebeat 就能读取数据,迅速发送到 Logstash 进行解析,亦或直接发送到 Elasticsearch 进行集中式存储和分析。
ELK部署架构
因为现在只有1台fortigate防火墙的日志需要交给ELK处理,为方便测试学习,故将ELK组件安装在一台测试服务器上。
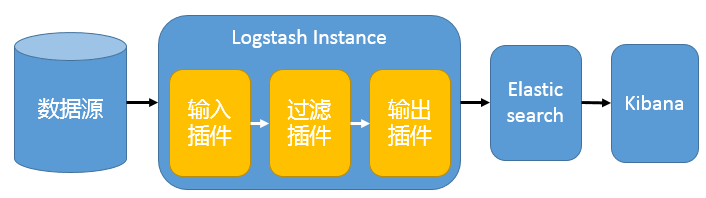
在这种架构中,只有一个 Logstash、Elasticsearch 和 Kibana 实例。Logstash 通过输入插件从多种数据源(比如日志文件、标准输入 Stdin 等)获取数据,再经过滤插件加工数据,然后经 Elasticsearch 输出插件输出到 Elasticsearch,通过 Kibana 展示。
继续阅读…
分类:虚拟化日期:2020-09-06 - 20:02:23评论:14条作者:老谢
通过部署Horizon虚拟化,用户可以在任何地方访问此环境,用户将桌面数据全部放置在数据中心服务器里,管理员可以进行集中式管理,从而提高效率和增强了安全性,并且可以使用配置较低的PC或瘦客户机访问虚拟桌面环境来降低成本。
组件
Horizon Client:包括Windows、MAC OS、Linux平台,可以让用户通过各种硬件来访问虚拟桌面
Horizon Agent:通过与Horizon Client连接来为用户提供连接监视,虚拟打印USB映射等功能
Horizon Connection Server:充当客户端的连接点,HCS通过Windows AD对用户提供身份验证,并将连接请求发到相应的虚拟机或服务器
Horizon Composer:从指定的父虚拟机创建链接克隆池,和vCenter可以安装在同一台服务器上,用来管理虚拟镜像,节约磁盘资源
Horizon ThinApp:将应用程序封装到虚拟化的沙箱中
Client Device:客户通过笔记本、PC、瘦客户端设、MAC或平板访问虚拟桌面,只要打开Horizon Client就能显示Horizon的桌面。瘦客户端借助瘦客户端软件,管理员可以进行配置,让Horizon Client成为用户在瘦客户端上唯一能直接启动的应用程序,将传统PC作为瘦客户端使用
规划
|
服务器类型
|
计算机名称
|
ip地址
|
所需软件
|
|
vSphere ESXi
|
esxi-01
|
192.168.1.101
|
VMware-VMvisor-Installer-6.7.0.update03-14320388.x86_64-DellEMC_Customized-A02.iso
|
|
vSphere ESXi
|
esxi-02
|
192.168.1.102
|
VMware-VMvisor-Installer-6.7.0.update03-14320388.x86_64-DellEMC_Customized-A02.iso
|
|
vSphere ESXi
|
esxi-03
|
192.168.1.103
|
VMware-VMvisor-Installer-6.7.0.update03-14320388.x86_64-DellEMC_Customized-A02.iso
|
|
vSphere vCenter
|
vc.silyer.net
|
192.168.1.121
|
VMware-VCSA-all-6.7.0-15132721.iso
|
|
Domain Controller
|
view-ad.silyer.net
|
192.168.1.131
|
cn_windows_server_2012_r2_vl_x64_dvd_2979220.iso
|
|
Connection Server
|
view-connect.silyer.net
|
192.168.1.132
|
cn_windows_server_2012_r2_vl_x64_dvd_2979220.iso
VMware-Horizon-Connection-Server-x86_64-7.12.0-15770369.exe
|
|
Composer Server
|
view-composer.silyer.net
|
192.168.1.133
|
cn_windows_server_2012_r2_vl_x64_dvd_2979220.iso
VMware-viewcomposer-7.12.0-15747753.exe
cn_sql_server_2012_standard_edition_x86_x64_dvd_813404.iso
|
|
View Clone Agent
|
vwin7-agent.silyer.net
|
DHCP
|
cn_windows_7_enterprise_with_sp1_x64_dvd_u_677685.iso
VMware-Horizon-Agent-x86_64-7.12.0-15805436.exe
|
继续阅读…
分类:linux日期:2020-05-12 - 21:22:20评论:2条作者:老谢
不知道哪位大神最近在做法机房攻击频发,一被攻击路由就绕路,为了监控发生频率故需对路由进行监控,思路为使用BESTTRACE来追踪理由,利用bash脚本对追踪结果进行分析,并交由zabbix做映射值。
安装BESTTRACE
BESTTRACE是ipip.net推出的Linux版路由追踪工具,可以替代traceroute命令,该工具可以输出json数据,及查ip所属地和AS号,但实际情况发现查询频率过高,会导致返回503错误,可能是ipip.net做了请求限制,避免滥用。
wget http://cdn.ipip.net/17mon/besttrace4linux.zip
unzip besttrace4linux.zip
chmod +x besttrace
mv besttrace /usr/sbin/
chmod +s /usr/sbin/besttrace |
wget http://cdn.ipip.net/17mon/besttrace4linux.zip
unzip besttrace4linux.zip
chmod +x besttrace
mv besttrace /usr/sbin/
chmod +s /usr/sbin/besttrace
外部脚本监控
cd /usr/local/zabbix/share/zabbix/externalscripts
vim besttrace.sh
#!/bin/bash
IP=$1
var=$RANDOM
/usr/sbin/besttrace -q 1 -l -a $IP > /tmp/besttrace/tmp.$var
if [ `grep -c -E 'jp|tko' /tmp/besttrace/tmp.$var` != 0 ]; then
if [ `grep -c -E '219.158' /tmp/besttrace/tmp.$var` != 0 ]; then
echo "1"
else
echo "2"
fi
elif [ `grep -c -E 'us' /tmp/besttrace/tmp.$var` != 0 ]; then
if `grep -c -E '219.158' /tmp/besttrace/tmp.$var` != 0 ]; then
echo "3"
else
echo "4"
fi
elif [ `grep -c -E 'he.net' /tmp/besttrace/tmp.$var` != 0 ]; then
echo "5"
else
echo "0"
fi
rm -rf /tmp/besttrace/tmp.$var |
cd /usr/local/zabbix/share/zabbix/externalscripts
vim besttrace.sh
#!/bin/bash
IP=$1
var=$RANDOM
/usr/sbin/besttrace -q 1 -l -a $IP > /tmp/besttrace/tmp.$var
if [ `grep -c -E 'jp|tko' /tmp/besttrace/tmp.$var` != 0 ]; then
if [ `grep -c -E '219.158' /tmp/besttrace/tmp.$var` != 0 ]; then
echo "1"
else
echo "2"
fi
elif [ `grep -c -E 'us' /tmp/besttrace/tmp.$var` != 0 ]; then
if `grep -c -E '219.158' /tmp/besttrace/tmp.$var` != 0 ]; then
echo "3"
else
echo "4"
fi
elif [ `grep -c -E 'he.net' /tmp/besttrace/tmp.$var` != 0 ]; then
echo "5"
else
echo "0"
fi
rm -rf /tmp/besttrace/tmp.$var
映射值
0 ⇒ 正常
1 ⇒ 联通-日本
2 ⇒ 电信-日本
3 ⇒ 联通-美国
4 ⇒ 电信-美国
5 ⇒ he.net
bash写的太烂,各位大佬指正。
分类:linux日期:2020-04-07 - 11:25:15评论:2条作者:老谢
首先要确认Nginx有没有编译stream模块进去,使用nginx -V来查看,如果看到–with-stream则表示编译进去了,如果没用重新编译加入stream参数即可,配置字段要加到nginx.conf下面:
stream {
server {
listen 12345;
proxy_pass 1.1.1.1:1111;
proxy_buffer_size 512k;
proxy_connect_timeout 30s;
proxy_timeout 30s;
#allow 127.0.0.0/24;
#deny all;
}
server {
listen 1083;
proxy_pass 2.2.2.2:1080;
proxy_buffer_size 512k;
proxy_connect_timeout 30s;
proxy_timeout 30s;
#allow 127.0.0.0/24;
#deny all;
}
} |
stream {
server {
listen 12345;
proxy_pass 1.1.1.1:1111;
proxy_buffer_size 512k;
proxy_connect_timeout 30s;
proxy_timeout 30s;
#allow 127.0.0.0/24;
#deny all;
}
server {
listen 1083;
proxy_pass 2.2.2.2:1080;
proxy_buffer_size 512k;
proxy_connect_timeout 30s;
proxy_timeout 30s;
#allow 127.0.0.0/24;
#deny all;
}
}
listen:后面填写源端口(也就是当前服务器端口),默认协议为TCP,可以指定为
proxy_connect_timeout:连接超时时间
proxy_timeout:超时时间
proxy_pass:填写转发目标的IP及端口号
分类:linux日期:2020-03-05 - 10:26:39评论:0条作者:老谢
http://www.oracle.com/technetwork/java/javase/downloads/jdk8-downloads-2133151.html下载Linux x64 Compressed Archive版本最新的安装包。
tar -zxf jdk-8u241-linux-x64.tar.gz
mkdir /usr/local/java/
mv jdk1.8.0_241/ /usr/local/java/
vim /etc/profile |
tar -zxf jdk-8u241-linux-x64.tar.gz
mkdir /usr/local/java/
mv jdk1.8.0_241/ /usr/local/java/
vim /etc/profile
添加以下:
export JAVA_HOME=/usr/local/java/jdk1.8.0_241
export JRE_HOME=${JAVA_HOME}/jre
export CLASSPATH=.:${JAVA_HOME}/lib:${JRE_HOME}/lib
export PATH=${JAVA_HOME}/bin:$PATH |
export JAVA_HOME=/usr/local/java/jdk1.8.0_241
export JRE_HOME=${JAVA_HOME}/jre
export CLASSPATH=.:${JAVA_HOME}/lib:${JRE_HOME}/lib
export PATH=${JAVA_HOME}/bin:$PATH
source /etc/profile
ln -s /usr/local/java/jdk1.8.0_241/bin/java /usr/bin/java
java -version |
source /etc/profile
ln -s /usr/local/java/jdk1.8.0_241/bin/java /usr/bin/java
java -version




最新评论
Mr.Chou:18 19年入手的房子现在死的心都有了...
老何:不至于跌得这么狠吧
Andy烧麦:这些大厂都能提供必要的售后
王光卫博客:小米生态还是比较丰富
空空裤兜:在天猫买的利维斯顿,阿里智能APP...
林羽凡:我突然发现,你也记录了很多博文了。
菊座:小米的东西还行
zwwooooo:一般电器产品都jd,就是想售后身心
zwwooooo:能随便搞个公司玩玩也算是实力选手
大D:坚持就是胜利哈哈哈